Autymate is committed to providing a highly secure and reliable integration and business automation service. This includes maintaining the confidentiality of its customers' information and ensuring that customers' data will be available when it is needed. We use proven, tested, best-in-class security tools, technologies, practices, and procedures to achieve this.
Compliance
CyberGRX Audited
Autymate has successfully completed a 3-month security, disaster recovery audit by CyberGRX (https://www.cybergrx.com/).
We passed the audit for a large account at a Bank that required us to go through 3-month security, disaster recovery audit by a company called CyberGRX the world's largest third-party cyber risk exchange. They validated us on 26 control measures and had us go through an intensive review that required us to provide proof of all of our measures. We passed with flying colors. See the results below. In this process, we had to prove how we handle security, disaster recovery, failover, etc...
We scored 94% between all Security Measures:
Below you can see that we scored very low risk on 26 different security measures ranging in the categories of Strategic, Operation, Core, and Management controls for security and disaster recovery.
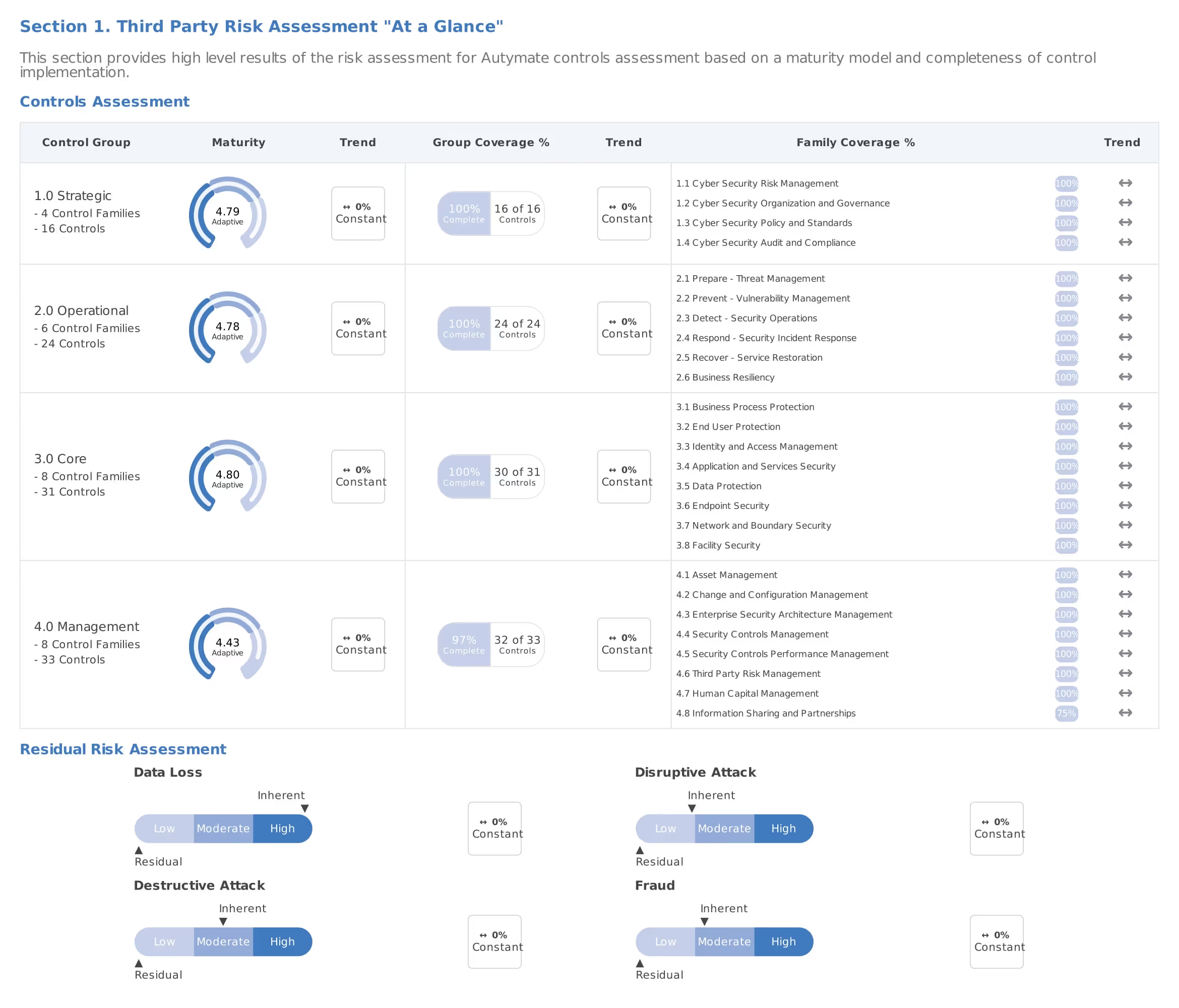
As you can see above there is little security residual risk in the areas of Data Loss, Destructive Attack, and Fraud, based on the intensive security review that Autymate has completed.
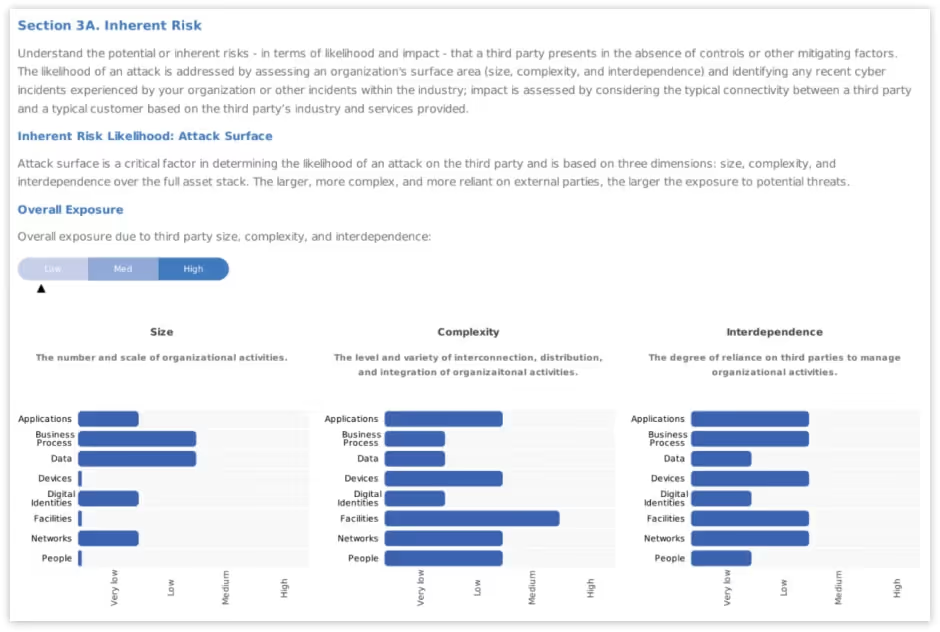
As you see above based on the security review the overall exposure to risk is Low.
Here is the full 46-page CyberGRX vendor assessment report: LINK
Having this kind of validation in hand streamlines the validation process of Autymate and gives you the assurance you need to know your data is safe with Autymate.
PCI
Autymate uses PCI Compliant Level 1 audited payment processor Stripe for processing credit card payments for the Autymate services.
Hosting Environment and Physical Security
Autymate is hosted on public cloud infrastructure from Amazon Web Services (AWS). Both Amazon undisputedly maintains the highest standards of security for their data centers. You can read further about AWS here:
aws.amazon.com/security/
HIPAA Compliance
AUTYMATE has demonstrated compliance with federal HIPAA regulation by completing Compliancy Group's proprietary 6-Stage HIPAA Risk Analysis and remediation process. Read the full post here LINK.
Network Security
The Autymate website is only accessible over HTTPS. Traffic over HTTPS is encrypted and is protected from interception by unauthorized third parties. Autymate follows current best practices for security, including the use of robust encryption algorithms with a key length of at least 128 bits.
Autymate also uses secure protocols for communication with third-party systems: usually HTTPS, but other protocols such as SFTP and FTPS are also supported. For on-premise systems, access requires installing an on-premises agent behind the firewall, which communicates outbound to Autymate over an encrypted link, using TLS 1.2.
Autymate uses a multi-tier architecture that segregates internal application systems from the public Internet. Public traffic to the website passes through a Web Application Firewall (WAF) and then is routed to internal systems running on private subnets. Interior, as well as exterior network traffic, uses secure, encrypted protocols. All network access, both within the data center and between the datacenter and outside services, is restricted by firewall and routing rules. Network access is recorded into a centralized, secure logging system.
Authentication
Clients login to Autymate using a password that is known only to them. Password length, complexity, and expiration standards are enforced. Passwords are not stored; instead, as is standard practice, only a secure hash of the password is stored in the database. Because the hash is relatively expensive to compute, and because a "salting" method is used, brute-force guessing attempts are relatively ineffective. Password reverse-engineering is complicated even if the hash value were to be obtained by a malicious party.
Autymate users can optionally configure their accounts to use Two-Factor Authentication utilizing an authenticator app such as Google Authenticator, Microsoft Authenticator, or Authy.
Autymate supports integration with 3rd party SAML compliant SSO systems. This allows an enterprise to manage access to Autymate as well as other enterprise applications and apply custom authentication schemes and policies.
Autymate also supports Single Sign-On using 3rd-party credentials, including Google and Microsoft Office 365.
Autymate supports automatic session logout after a period of time. Enterprises can set the appropriate timeout period according to their security needs.
When Autymate recipes connect to remote systems using user-supplied credentials, where possible, this is done using OAuth2. In those cases, no certificates need to be stored in the Autymate system. However, if a remote system requires credentials to be stored, they are encrypted using a 256-bit key.
Application Development and Testing
Autymate has a comprehensive software development lifecycle process that incorporates security and privacy considerations. Design and code reviews and unit and integration testing are part of the process.
Autymate undergoes an annual penetration test of the website by a qualified third party. Also, regular internal vulnerability scans are conducted.
Data Privacy
Autymate has a public privacy policy, which details the types of personal information we collect, our handling of this information, and our customers' privacy rights.
Transaction Data Retention and At-Rest Protection
All data stored in the Autymate system is encrypted at rest.
Autymate stores transaction-related data for a limited period to provide visibility into system activity, facilitate testing and debugging, allow re-running of failed transactions, and support long-running transactions. All transaction data is always encrypted in transit and when stored in Autymate's platform. Autymate stores transaction data in Google Cloud.
Customers have control over the retention period of the transaction data. Also, Autymate provides the ability to mask out sensitive data in the transaction logs for additional security.
Incident Response
Autymate has deployed a variety of security and monitoring tools for its production systems. There is 24x7 monitoring of its systems' security status, and automated alerts are configured for security and performance issues.
While we don't anticipate there ever being a breach of our systems, Autymate has put in place a Security Incident Response Plan, which details roles, responsibilities, and procedures in case of any actual or suspected security incident.
Our Organization
All employees are subject to background checks that cover education, employment, credit, and criminal history. Employment at Autymate requires written acknowledgment by employees of their roles and responsibilities for protecting user data and privacy.
Autymate maintains an information security training program that is mandatory for all employees.
Knowledgeable full-time security personnel are on staff.


