Autymate
Cyber Security Risk Assessment

CyberGRX Security/DR Audit
We recently passed a 3-month security and disaster recovery audit by CyberGRX,the world's largest third-party cyber risk exchange as requested by one of our large client account. CyberGRX validated us on all 30 control measures.
We passed with flying colors. See the results below.
In this process, we had to prove and document how we handle security, disaster recovery, failover, etc...
You can obtain a copy of the report directly from CyberGRX. Alternatively, We have provided a copy of this extensive report for you to review.
We scored 94% between all Security Measures:
*Click on image to zoom in
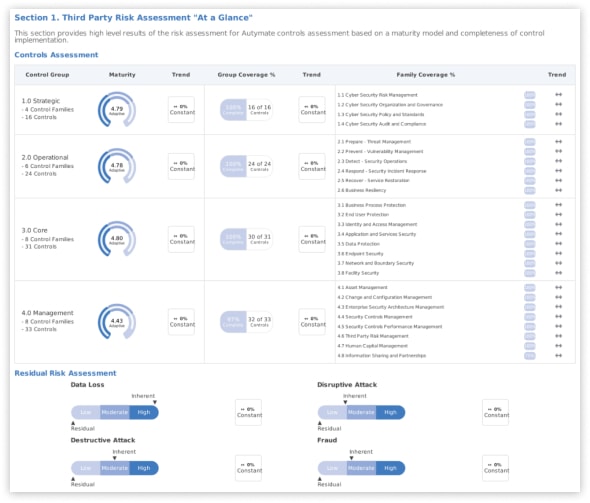
Assessment results
Explore the results of the CyberGRX audit and assessment.
Inherent risk
Understand the potential or inherent risks - in terms of likelihood and impact - that a third party presents in the absence of controls or other mitigating factors.
The likelihood of an attack is addressed by assessing an organization's surface area (size, complexity, and interdependence) and identifying any recent cyber incidents experienced by your organization or other incidents within the industry; impact is assessed by considering the typical connectivity between a third party and a typical customer based on the third party’s industry and services provided.
*Click on image to zoom in
Above you can see that we scored very low risk on 26 different security measures ranging in the categories of Strategic, Operation, Core, and Management controls for security and disaster recovery.
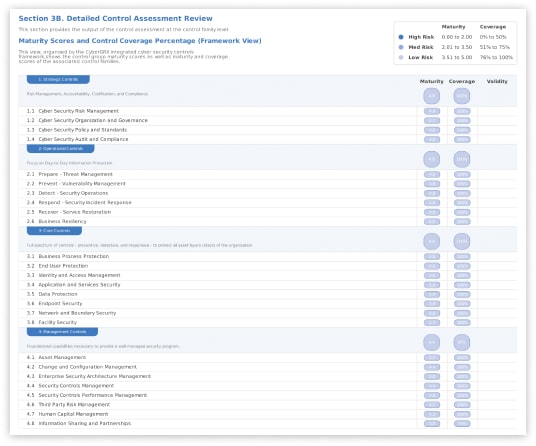
Control assessment
Understand the potential or inherent risks - in terms of likelihood and impact - that a third party presents in the absence of controls or other mitigating factors.
The likelihood of an attack is addressed by assessing an organization's surface area (size, complexity, and interdependence) and identifying any recent cyber incidents experienced by your organization or other incidents within the industry; impact is assessed by considering the typical connectivity between a third party and a typical customer based on the third party’s industry and services provided.
*Click on image to zoom in
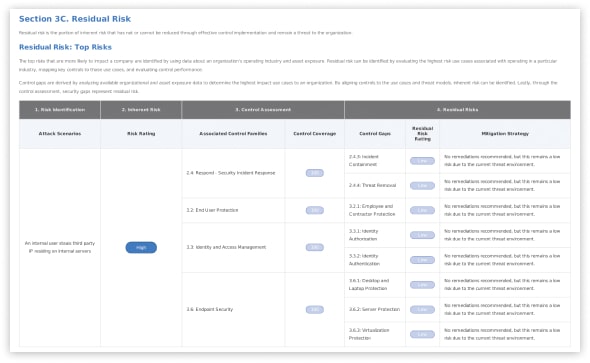
Residual risk
Understand the potential or inherent risks - in terms of likelihood and impact - that a third party presents in the absence of controls or other mitigating factors.
The likelihood of an attack is addressed by assessing an organization's surface area (size, complexity, and interdependence) and identifying any recent cyber incidents experienced by your organization or other incidents within the industry; impact is assessed by considering the typical connectivity between a third party and a typical customer based on the third party’s industry and services provided.
*Click on image to zoom in
HIPAA Security

Certified HIPAA compliant to ensure peace of mind.
Security is at the top of every executive’s mind. Autymate has taken the extra steps to ensure what’s private stays private. We utilize industry best-practices for transferring, storing, and accessing patient data, with years of experience working in hospitals and medical practices.

Certified HIPAA compliant to ensure peace of mind.
Security is at the top of every executive’s mind. Autymate takes extra steps to ensure what’s private stays private.
We utilize industry best-practices for transferring, storing, and accessing patient data, informed by years of experience working in hospitals and medical practices.